Security Assessment Template
Template
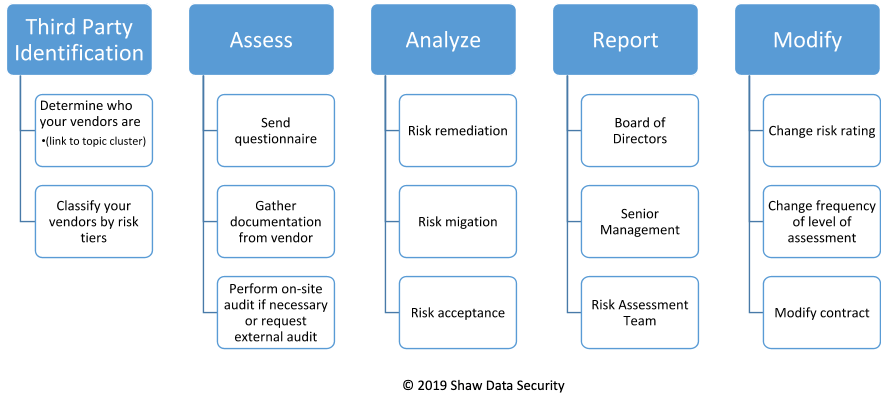
Third parties should be assessed during the vendor selection process, on a regular schedule, and/or in response to an external event as a data breach. The scope of the services provided by the third party should dictate the frequency and level of assessment. Vendors with access to highly sensitive data should have more in-depth assessment.